Can Trojans be spyware?
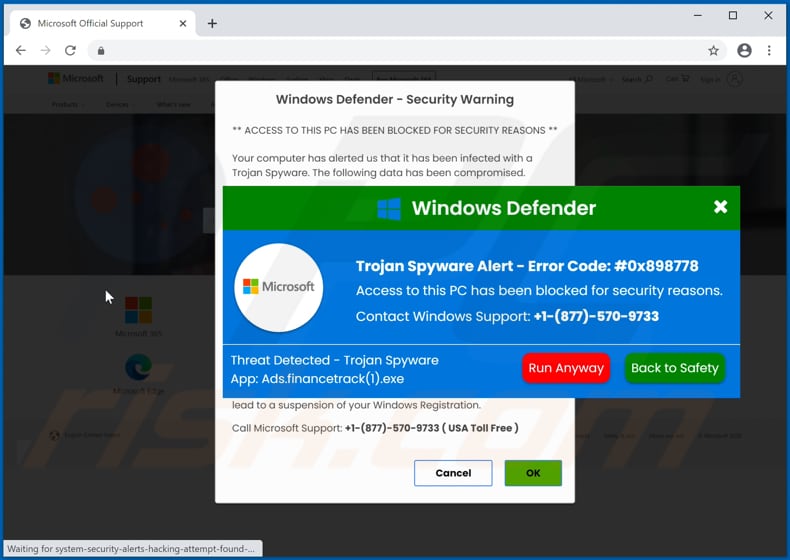
Are Trojans spyware
Spyware is software that observes user activities, collecting sensitive data like account credentials or banking details. They send this data back to the attacker. Spyware is typically disguised as useful software, so it is generally considered as a type of trojan.
Is Trojan horse A virus or spyware
A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program.
Can malware be spyware
Spyware is one type of malware that can monitor or control your computer use. It may be used to send consumers pop-up ads, redirect their computers to unwanted websites, monitor their Internet surfing, or record their keystrokes, which, in turn, could lead to identity theft.
What is the difference between Trojan malware and spyware
The main objective of the spyware is to monitor the activity of the system. The main objective of the trojan horse is to control the activity of the system.
Can a Trojan virus track you
Once a trojan horse is installed on your computer, it can spy on you, steal your personal information, and/or create backdoors that allow other hackers to do the same.
Can a Trojan virus record you
Cybercriminals can use so-called Trojan horse malware. You click on an attachment or download a piece of music or video infected with malware, and hey presto! – A cybercriminal can remotely control your PC's functions – including your camera and microphone and may even be able to record images and audio remotely.
How does Trojan spyware work
A Trojan Horse (Trojan) is a type of malware that disguises itself as legitimate code or software. Once inside the network, attackers are able to carry out any action that a legitimate user could perform, such as exporting files, modifying data, deleting files or otherwise altering the contents of the device.
How illegal is spyware
Surreptitiously installing spyware onto another person's computer or cell phone is illegal. With limited exceptions, recording telephone conversations without consent is illegal. Tracking another person with a GPS device is likewise illegal, unless there is consent. How to detect spyware.
What are spy apps disguised as
Android spyware pretends to be Google to avoid detection and removal. Android spyware disguises itself as Google Play, Youtube, Google, or a VOIP calling app Botim and is almost impossible to remove from a phone.
What causes Trojan spyware
But it will also install the harmful virus on your computer in the background. Be careful when you get files from the following sources. Many users install trojans from file-sharing websites and fake email attachments. You can also get attacked from spoofed chat messages, infected websites, hacked networks and more.
What is an example of Trojan spyware
Examples of Trojans
Zeus – Also known as Zbot, Zeus is a successful Trojan malware package with many variants used to carry out a number of different types of attack. It's perhaps most well-known for its successful hack of the U.S. Department of Transportation.
Is Trojan virus easy to detect
Since Trojans often imitate legitimate system files, they are very difficult to find and eliminate using conventional virus scanners. But if a Trojan is not found, it can cause considerable damage to the operating system and the people and companies behind it.
Can Trojan infect your Wi-Fi
A trojan attack tricks you into downloading malware hiding a virus that then tramples all over your phone, tablet, or computer. A router virus can ride inside a trojan, waiting to sniff out vulnerable public or home Wi-Fi networks to infect.
Can a Trojan steal my passwords
There are a variety of types of Trojans, many of which can launch sophisticated and clever attacks. Here are some types to be aware of: Password-stealing Trojans—These look for saved passwords on your computer and email them to the hackers. Some can even steal passwords cached in your browser history.
Can spyware see you
Spyware is software that secretly infects your computer to monitor and report on your activity and provide information to a third party. It might track websites you visit, files you download, your location (if you're on a smartphone), your emails, contacts, payment information or even passwords to your accounts.
Is spyware a rat
A Remote Access Trojan, otherwise known as a RAT, is a type of spyware that allows a cybercriminal to take control of the computer or other device it's installed on. RATs are malicious software that constitute a major cybersecurity threat.
Can apps secretly spy on you
Spyware apps surreptitiously run on a device, most often without the device owner's awareness. They collect a range of sensitive information such as location, texts and calls, as well as audio and video. Some apps can even stream live audio and video.
Can spyware be detected
Run a malware scan: There are mobile antivirus solutions available that can detect and remove spyware. This is the easiest solution available, but it may not be effective in every case. Cybersecurity vendors, including Malwarebytes, Avast, and Bitdefender, all offer mobile spyware-scanning tools.
Are Trojan viruses detectable
To find it, the user must initiate a full computer scan with an anti-virus scanner. This should be able to identify all threats and inform the user of the name of the malware. In addition, the scanner usually recommends the necessary measures to completely remove the Trojan and the installed malware from the system.
Should I be scared of Trojan virus
In the cybersecurity world, Trojan malware seems to be harmless — and even useful — but really, it has a malicious agenda. Trojans are disguised as legitimate files, but they have one goal: to trick you into clicking, opening or installing them.
Is it OK to have Trojan virus
Trojans can infect your computer and cause enormous problems before you even know what happened. Once a trojan gets onto your system, it can monitor your keyboard, install additional malware and cause a variety of other problems you simply don't want to face.
Can spyware see incognito
In addition, incognito mode does not protect you against cyberattacks such as phishing, malware, or viruses. If you already have spyware installed on your device, it can still track your activity and steal sensitive information, even in incognito mode.
Can apps see you through your camera
All sorts of apps can request permission to access the camera, microphone, and other features, such as location information, on your phone or computer. Using the steps below, it's easy to see which apps have requested permission and revoke permissions that you've granted in the past.
What removes spyware
antivirus
The best way to remove spyware is to use an anti-spyware scanner. Download and install a reliable free antivirus solution, and it will detect and remove the spyware from your device.
Can Trojans be fake
Fake antivirus Trojans
A dangerous type of scareware, fake AV Trojans pretend to detect viruses and other malware on your device, then urge you to pay for security software — which is either useless or actively malicious.


0 Comments